A new attack vector that could compromise GitHub repositories has been uncovered by researchers at Palo Alto Networks’ Unit 42 team. The vulnerability, which exploits GitHub Actions artifacts generated during CI/CD workflows, could potentially grant high-level access to cloud environments.
The researchers found that a combination of misconfigurations and security flaws can cause artifacts to leak tokens, including those for third-party cloud services and GitHub itself. These tokens become accessible to anyone with read access to the repository, allowing malicious actors to potentially compromise the services to which these secrets grant access.
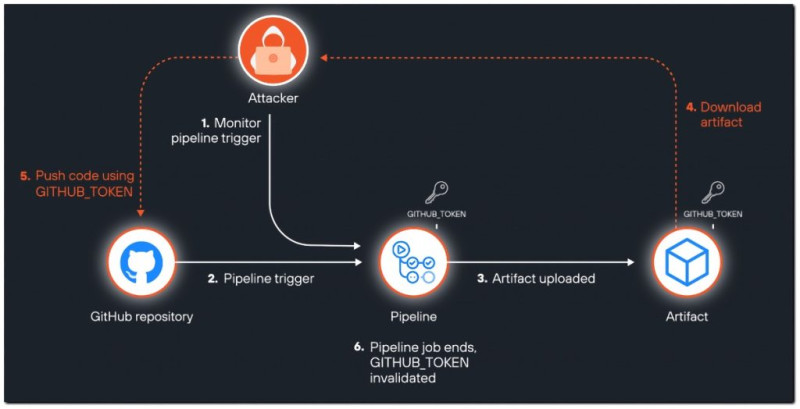
In most of the vulnerable projects discovered, the most common leakage was of GitHub tokens. This could allow an attacker to act against the triggering GitHub repository, potentially pushing malicious code that could flow to production through the CI/CD pipeline, or accessing secrets stored in the GitHub repository and organisation.
While the research applies to both private and public GitHub repositories, the team focused on discovering vulnerable public repositories. They uncovered high-profile open-source projects owned by some of the world’s largest companies, which could have potentially impacted millions of consumers before mitigation.
All disclosed cases were reported to the maintainers of these projects, with the researchers receiving excellent support from all teams. Collaboration ensued to mitigate all discoveries quickly and efficiently.
The researchers explored workflow artifacts, a feature in GitHub Actions that allows for persisting and sharing data across jobs within the same workflow. These artifacts can include any files generated during the build process, such as compiled code, test reports, or deployment packages.
The team compiled a list of popular open-source projects on GitHub and automated the process of downloading their artifacts and scanning them for secrets. Their hunch proved correct, as they found working tokens for various cloud services, including music streaming and cloud infrastructure.
More interestingly, they discovered various GitHub tokens. Two types of tokens kept appearing: GITHUB_TOKEN (with a prefix of ghs_) and ACTIONS_RUNTIME_TOKEN (a JWT token).
The researchers found that these tokens weren’t part of the repository code but were only found in repository-produced artifacts. They identified that the default behaviour of the widely-used actions/checkout GitHub action persists credentials, writing the GITHUB_TOKEN to the local git directory.
Many users unknowingly upload their entire checkout directory as an artifact, including the hidden .git folder containing the persisted GITHUB_TOKEN. This leads to publicly accessible artifacts containing the GITHUB_TOKEN.
Another issue arose from the use of super-linter, a popular open-source code linter. When its CREATE_LOG_FILE property is set to ‘True,’ it creates a log file that includes environment variables, potentially exposing sensitive tokens.
The researchers developed a method to abuse leaked GitHub tokens, particularly the ACTIONS_RUNTIME_TOKEN, which has an expiration of about six hours. They automated a process to download an artifact, extract the token, and use it to replace the artifact with a malicious one.
GitHub’s announcement of version 4 of the artifacts feature allows for downloading artifacts while the workflow run is in progress. This created a potential race condition, enabling the leaked GITHUB_TOKEN to be downloaded, extracted, and used before the job finished and the token expired.
The researchers successfully exploited this vulnerability in several open-source projects, including those maintained by major organisations like Google, Microsoft, Red Hat, and Canonical.
All affected open-source projects cooperated swiftly to patch their code when approached about the issue. Some even offered bounties and merchandise as a thank you for the disclosure.
To address these concerns, the researchers developed a proof of concept custom action called upload-secure-artifact. This action adds a crucial security layer by auditing the source directory for secrets and blocking the artifact upload when there’s a risk of accidental secret exposure.
Organisations using the artifacts mechanism are urged to reevaluate their usage, especially in light of GitHub’s deprecation of Artifacts v3.
(Photo by Mohammad Rahmani)
See also: GitHub’s Copilot Autofix triples vulnerability remediation speed

Want to learn more about cybersecurity and the cloud from industry leaders? Check out Cyber Security & Cloud Expo taking place in Amsterdam, California, and London. The comprehensive event is co-located with other leading events including BlockX, Digital Transformation Week, IoT Tech Expo and AI & Big Data Expo.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.
Tags: coding, cyber security, cybersecurity, development, git, github, GitHub actions, hacking, programming, repo, security, unit 42, vulnerability